
Managed Cybersecurity
While ransomware and cyber-crime in general has only entered the common zeitgeist relatively recently, largely driven by a number of high-profile attacks both at home and abroad, as a concept it isn’t anything new. As the saying goes, “There’s nothing new under the sun”; in 2023 this even applies to an industry as rapidly evolving as IT, which witnessed the first incidents of ransomware as early as the 1980s. In this article, we’ll explore:
- Some of the basic principles of cyber-attacks,
- The evolving threat environment,
- Recommendations on how organisations can approach cybersecurity as a business-level investment,
- The benefits of enhanced 24/7 Managed Detection and Response (MDR) services
Basic principles of cyber-attacks
While the actual tools and threat models have evolved a lot over the years, the fundamental high-level steps involved in the successful execution of cyber-attacks such as ransomware remains unchanged: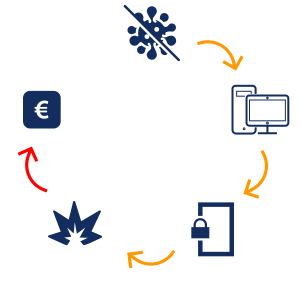
- The attacker manages to implant malware onto a user’s device, often through deceptive measures such as phishing or social engineering tactics.
- The malware calls home over a secured communications channel to the attacker, allowing them to freely move about their victim’s device with ease.
- A pair of unbreakable cryptographic keys, one on the victim’s device and the other held by the criminal, are generated.
- The ransomware detonates, encrypting files, folders, applications and data across the victim’s network, rendering them utterly useless.
- The dreaded ransom note appears on the victim’s screen demanding payment, often in the form of untraceable cryptocurrency, within a designated timeframe or face dire consequences, which can include permanent deletion of the decryption key and/or dissemination of sensitive information across the dark web.
Basic Principle, Evolving Threat
Although the basic framework hasn’t changed much over the last 30+ years, the specific tactics, organisation and veracity of hostile actors has certainly evolved.
As the complexity of many organisation’s IT infrastructures has grown, often featuring multiple combinations of architectures and operating systems, the ingenuity and competency of threat actors has developed at pace. More complex malware with cross-platform infection capabilities is becoming the norm, allowing cybercriminals to engage in “Big Game Hunting”, with the aim of totally compromising even complex and diverse IT infrastructures.
Where once ransomware was largely the purview of individual crime syndicates, in recent years the space has evolved with threat actors coalescing around common practices and goals, forming a well-organised global industry. “Ransomware-as-a-Service” or “RaaS” is an example of this industrial development. In a twisted parody of legitimate software companies, malware developers sell their code to others on the dark web, even going as far as to provide instruction and tech support to help their “customers” execute a successful attack.
The rise of Initial Access Brokers (IABs) is another contributing factor which has led to heightened concerns around ransomware. IABs are criminal groups who specialise in illegitimately infiltrating organisation’s IT systems and then selling this access information to other groups. IABs have allowed ransomware criminals to specialise in the sophistication and complexity of attack executions without needing to worry about making the initial infiltration. IABs rarely discriminate in those they do business with, which can lead to some unfortunate organisations being hit with ransomware multiple times in quick succession, from different groups.
Approach Cybersecurity as a Business-Level Investment
Despite the surface level changes in the attack methods and tactics, being prepared to defend against attacks at a high level remains the same.
Many organisations are starting to take cybersecurity more seriously. However, misplaced effort, no matter how well intended, often leads to the wrong outcome. A common mistake we see organisations make is the “ground-up” approach; hyper-focusing on point-security solutions with the expectation that they will solve all their security woes. In reality, the very opposite approach should be taken; cybersecurity needs to be a top-down, data-driven decision. Before even considering what additional security services are required, organisations need to have a fundamental, thorough understanding of their IT assets, more so than any attacker. This knowledge is the defender’s greatest advantage in the fight against cybercrime. In adopting the defender’s mind set, each and every one of these assets should be viewed as potential avenues for attack.
Once a thorough cataloguing of IT systems has been complete, equally important is knowing the data itself. Where is it stored? Who has access to it? Does it contain personally identifiable or otherwise sensitive information? Not to mention the task of realising the consequences to the organisation as a whole should this data be stolen or irreparably destroyed – competitive loss, reputational damage and regulatory consequences, to name but a few.
Only when due diligence has been followed by getting this base-level understanding can an organisation make informed decisions on how to protect their ecosystem. Again, simply installing a single security product and washing one’s hands of the concern isn’t enough. Defences need to be layered intelligently, with multiple redundancies and fail-safes built into the process to block the efforts of an attacker at each stage of a cyberattack.
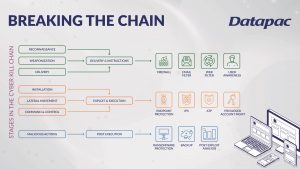
Managed Detection and Response (MDR)
While ensuring an organisation’s cybersecurity may seem straightforward as a high-level concept, in reality the levels of complexity quickly compounds, both in terms of implementing and appropriate security ecosystem and ensuring ongoing maintenance and monitoring. For this very reason, organisations across the world, large and small, public and private sector, are turning to the expertise and experience of outsourced Managed Detection and Response (MDR) service providers.
As already outlined, providing comprehensive security for one’s organisation involves careful consideration to select a suite of security tools and solutions which are synergistically layered to provide the best protection. The other half of the equation is the human element – does an organisation have the necessary skills and resources in-house to provide comprehensive, 24/7/365 threat monitoring, detection and elimination?
The answer for many is, unfortunately, no. There is still a significant IT skills shortage and specific cyber-security skills are even more scarce. Even if organisations have the capacity to provide in-house threat monitoring during business hours it still doesn’t address the requirement gap. Cyber-criminals are aware of this critical weakness and will deliberately time their attack detonations to occur when there’s nobody there to take action – during the middle of the night, at the weekend, during public holidays etc. To a large extent, cybersecurity tools are only as good as the eyes watching them.
MDR services solve this challenge with machine-accelerated human-lead active threat hunting, detection and elimination. MDR services provide teams of seasoned, expert veterans well-versed in the threat environment to monitor for threats and indicators of compromise. These versatile, flexible services are designed to meet organisation’s unique requirements, giving control over the level of support provided, from detailed notification and guidance for internal teams to full scale incident response and neutralisation.
If you have any concerns about your organisation’s cybersecurity, please feel free to leave your details below for a free, no-risk no-obligations discussion with one of our experts
Follow us on LinkedIn and Twitter for more updates.
Register for upcoming events
-
 "At Barretstown, we rebuild the lives of children, and their families, affected by childhood cancer and other serious illnesses. We serve 5,000 campers a year and have 1200 volunteers each year. Communication is crucially important and Datapac has helped us to streamline, improve and ensure efficiency."
"At Barretstown, we rebuild the lives of children, and their families, affected by childhood cancer and other serious illnesses. We serve 5,000 campers a year and have 1200 volunteers each year. Communication is crucially important and Datapac has helped us to streamline, improve and ensure efficiency." -
 "Datapac has provided us with a fantastic product and world-class levels of service and support. Whenever people ask me about our experience with Datapac I’m always ready to sing their praises and I would happily recommend their services to any organisation."
"Datapac has provided us with a fantastic product and world-class levels of service and support. Whenever people ask me about our experience with Datapac I’m always ready to sing their praises and I would happily recommend their services to any organisation." -
 "For many years Datapac has been our sole supplier for the maintenance of Personal Computers and Peripherals in Ireland. Through their Service Centres in Wexford and Dublin, Datapac provides excellent support to our businesses throughout the country and consistently meets the SLA targets which we have set. The skill, expertise and experience of their engineers and other technical support personnel are of the highest standard."
"For many years Datapac has been our sole supplier for the maintenance of Personal Computers and Peripherals in Ireland. Through their Service Centres in Wexford and Dublin, Datapac provides excellent support to our businesses throughout the country and consistently meets the SLA targets which we have set. The skill, expertise and experience of their engineers and other technical support personnel are of the highest standard." -
 “The value of dealing with an HP Gold partner in this process can’t be underestimated. Datapac provide us with a local touch and can cover the full range of our IT requirements, but when there is a specific technical requirement like this, they can bring the specialist technical resources of HP to the table. HP and Datapac had a thorough discussion with us around our requirement - and had really done their homework - and then were able to provide us with a very highly specified test platform for us to prove the application on before we committed to purchase.”
“The value of dealing with an HP Gold partner in this process can’t be underestimated. Datapac provide us with a local touch and can cover the full range of our IT requirements, but when there is a specific technical requirement like this, they can bring the specialist technical resources of HP to the table. HP and Datapac had a thorough discussion with us around our requirement - and had really done their homework - and then were able to provide us with a very highly specified test platform for us to prove the application on before we committed to purchase.” -
 Datapac understands our needs and requirements and has the expertise and experience to follow through on all our requests. Our constant need to reduce costs has been assisted by Datapac's ability to suggest alternative solutions and methods whilst improving both efficiency and productivity. Our partnership with Datapac is akin to having an IT department on site that we simply could not provide ourselves.
Datapac understands our needs and requirements and has the expertise and experience to follow through on all our requests. Our constant need to reduce costs has been assisted by Datapac's ability to suggest alternative solutions and methods whilst improving both efficiency and productivity. Our partnership with Datapac is akin to having an IT department on site that we simply could not provide ourselves.